Create and protect your sensitive documents
Secure Office is a document management cyber security product that focuses on protecting classified information using machine learning, artificial intelligence, customizable access controls, and in-document Need-to-Know (N2K) security.
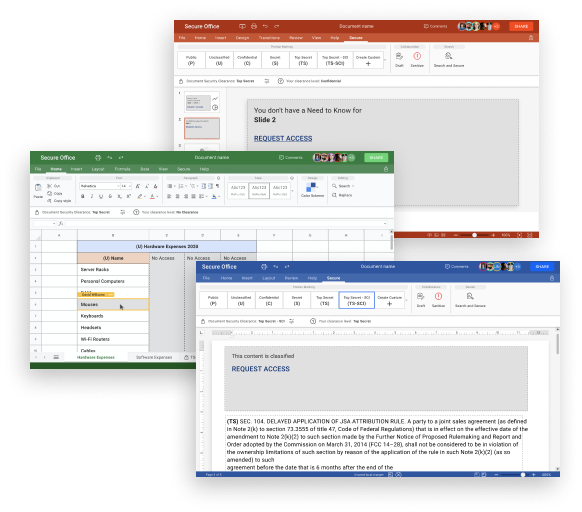
Share with people only what they Need to Know
Secure Office Need-to-Know (N2K) permission management system dynamically controls in-document security elements in real-time. You can protect an entire document, a specific section, or even a single word within a document using N2K. Users can collaborate on a document even if they have different permissions to its content. The data is protected in real-time on server-side basis.
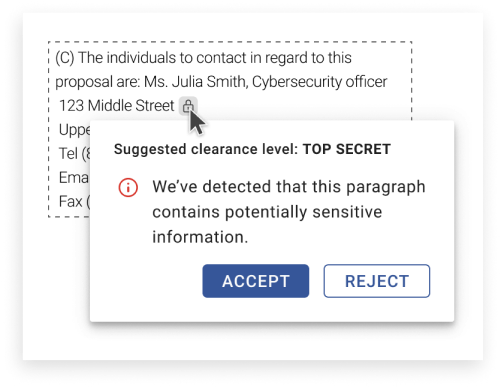
Detect data spillages before they turn into a threat
Secure Office utilizes a big data analysis engine that uses machine learning techniques to detect potentially sensitive information that is not sufficiently protected with the proper classification. The system automatically analyzes the entered text by advanced ML algorithms in real-time and suggests appropriate security classification. The ML engine also identifies data that is classified incorrectly.
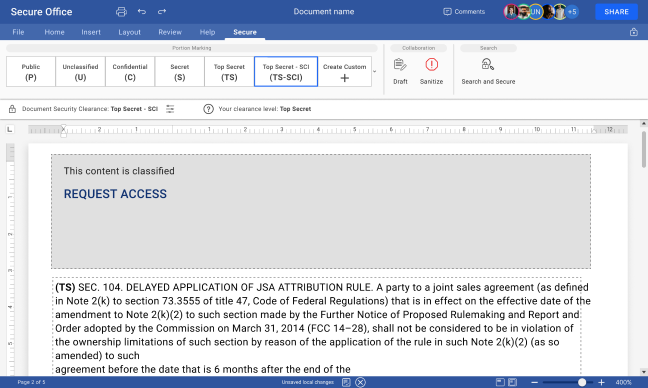
Create, protect, and collaborate on documents online
Secure Office provides a complete suite of online editors to create and collaborate on documents, regardless of format, in a web browser - text documents, spreadsheets, presentations, and whiteboards - and manage them using built-in Secure Drive file storage.
Documents
Create, edit, and collaborate on text documents using standard text editor features of a text editor.
Define custom permissions to:
- The whole document.
- Specific sections within the document.
- Specific paragraphs, sentences, or words.
- Inserted objects, like images or charts.
Automatically mark classified paragraphs with corresponding clearance-level abbreviations in accordance with legal requirements.
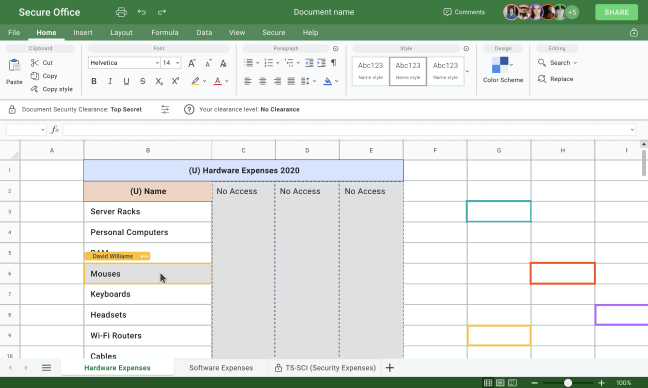
Spreadsheets
Create complex spreadsheets using built-in formulas, functions, diagrams, and other standard spreadsheet features, while collaborating in real-time.
Define custom permissions to
- The whole spreadsheet.
- Specific worksheets.
- Specific columns, rows, cell ranges, or individual cells.
- Inserted objects, like images or charts.
Automatically mark classified columns, rows, and cells with corresponding clearance-level abbreviations in accordance with legal requirements.
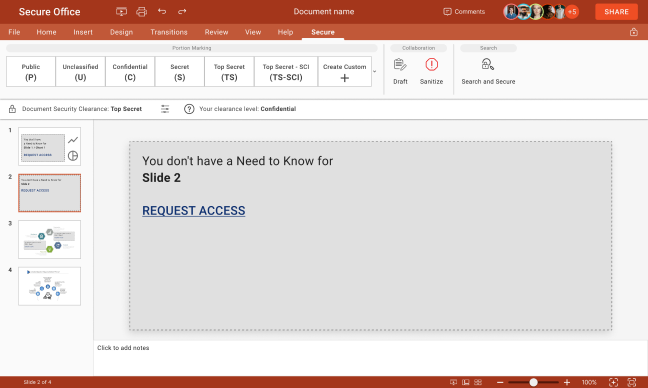
Presentations
Create colorful presentations using text, advanced graphics, and dynamic slide transitions.
Define custom permissions to:
- The whole presentation.
- Specific slides.
- Specific objects, like shapes, text boxes, or images.
Automatically mark classified slides and individual objects with corresponding clearance-level abbreviations in accordance with legal requirements.
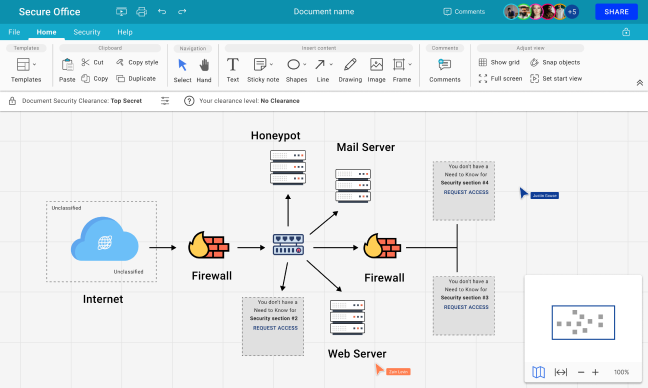
Whiteboard
Visualize anything you want on an infinite canvas. Create any type of visual content: process diagrams, architecture schemes, freehand drawings, inserted images, lists, sticky notes, and more.
Define custom permissions to:
- The whole whiteboard.
- Specific areas of the canvas.
- Specific objects, like shapes, text boxes, or images.
Automatically mark classified areas and individual objects with corresponding clearance-level abbreviations in accordance with legal requirements.
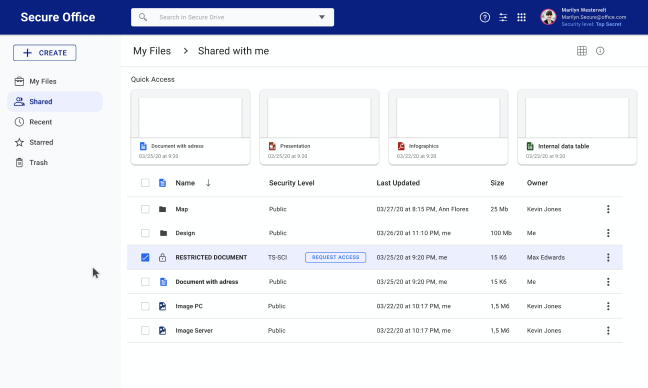
Secure Drive
Store, search, share, and manage files in a secure environment.
Use Secure Drive to ensure users can access only the documents and folders that match their security profile and clearance level.
The user only sees changes that conform to their document permissions and clearance level.
Guard your sensitive information with Machine Learning
Secure Office uses Machine Learning models to identify data that is improperly classified. As documents are loaded into Secure Drive, the models self-tune to the practices of the organization, improving document security.

Automated Spillage Detection
Secure Office contains a server-side big data analysis engine that uses the following ML capabilities to strengthen the product’s data-protection suite:
- Named Entity Recognition - NER: Identify occurrences where the same term has different classifications across multiple documents, helping you detect discrepancies in classification.
- Text similarity measurements – detection of contextual data spillage with word-2-vec approach.
- Summarization of the large text corpuses – 1 paragraph summary.
- Document clustering - recommend similar documents.
- Knowledge graph representation of the documents – see connections between documents and important entities from the documents.
Begin using Secure Office with ease
Compatibility
Upload your existing documents to Secure Drive. Secure Office is compatible with most popular file formats including Microsoft Office and Open Office.
Integration
Secure Office integrates with your user management and security clearance platforms to ensure users are only allowed to see what they need to see.
Data migration and control
Secure Office brings the data from your documents together into a single graph structure that allows you to reveal hidden relations between data and identify potential points of data spillage.
Data security
Secure Office can be used in both on - and off-premise installations. Secure Drive file storage secures all files in a safe environment. Access to Secure Drive is available to users with Secure Office accounts.
Scalability
The architectural design of Secure Office allows the system to be easily scaled.
Use Secure Office for teams of any size.
Customization
Create custom security profiles for different groups of users. Personalize the user interface according to your company design standards.